In this cyber world, we would love to feel secured while surfing
through internet from all kind of security concerns. To ensure this lets
take a look at the secure browsers that needs to be used.
- TOR Browser
If you’re looking for a browser that’s thought of everything security-wise, Tor Browser might be the browser for you. The Tor Browser handles your security
concerns down to the smallest detail.
Tor also offers other security measures such as the automatic deletion
of your browser history and cookies when you’re finished browsing, the
blocking of third-party trackers, and protection that includes three
layers of encryption for your web traffic, “as it passes over the Tor
network.”
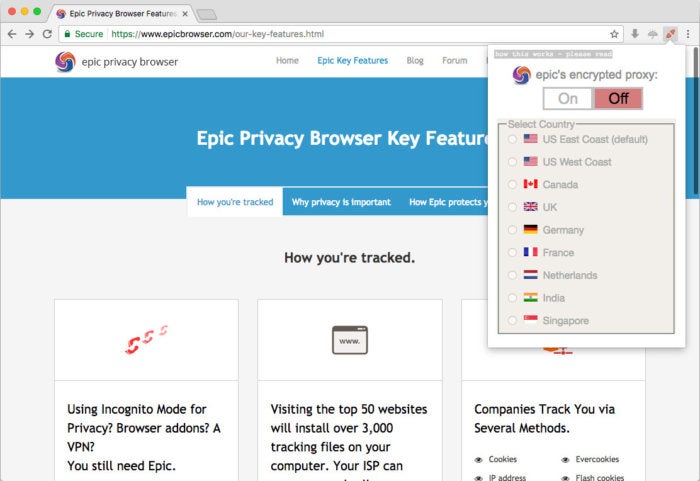
- Epic browser
Epic is built upon Chromium, the open-source project Google
and others
maintain. Google uses Chromium to provide the source code for its Chrome
browser. Epic takes several steps to increase
privacy by decreasing the amount of information the browser spills to
the outside world.
For
example, while rivals have manually enabled modes that automatically
delete all traces of browsing history — called "Incognito Mode" in
Chrome and "Private Browsing" in Firefox — Epic runs only in such
a mode. When a user closes Epic, swaths of otherwise-retained data is
automatically deleted, including all cookies, all browsing history and
all contents of the browser's cache.
- SRWare Iron Browser
 The SRWare Iron
is an interactive and easy to use freeware web browser. It is an
implementation of the Chromium by the Germany firm SRWare. The major
usage of this tool is to remove the various usage tracking and even
other kind of privacy related functionalities which Google Chrome has
got.
The SRWare Iron
is an interactive and easy to use freeware web browser. It is an
implementation of the Chromium by the Germany firm SRWare. The major
usage of this tool is to remove the various usage tracking and even
other kind of privacy related functionalities which Google Chrome has
got.
- Comodo Dragon Browser
Just like the Epic Privacy Browser, Comodo Dragon is based on the
Chromium project. The browser includes all Chrome’s features but
provides better security and privacy when browsing the web. So, if you
are not a huge fan of Chrome and prefer Mozilla instead, you can choose
Comodo Ice Dragon version as your most secure browser.
The main advantage of the browser are:
- Domain Validation technology that identifies secure SSL certificates;
- Blocks cookies and other tracking technologies;
- Stops Browser download tracking.
Stay safe and keep exploiting :)




Comments
Post a Comment