Basic hygiene check before installing/executing unknown file
· Filename
· File extension
Malware
analysis
Malware
analysis is the study or process of determining the functionality,
origin and potential impact of a given malware sample
such as a virus,
worm, trojan horse, rootkit, or backdoor. Malware or malicious
software is
any computer software intended to harm the host operating system or
to
steal sensitive data from users, organizations, or companies. Malware may
include software that gathers user information without permission.
TYPES
OF MALWARE ANALYSIS
Basic Static
Malware Analysis
· It consists of examining the executable file without
viewing
the actual instructions.
· It can confirm whether a file is malicious,
provide information about its functionality, and sometimes provide information
that will allow you to produce simple network signatures.
PROCESS OF BASIC STATIC
MALWARE ANALYSIS
·
Scan with AV
·
Identify file type
·
Check for pack
·
String Analysis
·
PE header Analysis
TOOLS USED
FOR BASIC STATIC ANALYSIS
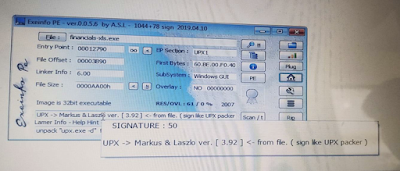
Exeinfo PE
·
It used to identify the type of file
·
It shows the signature value of
malware
·
It identifies the packet
UPX Tool
· UPX (Ultimate packet for executable)
· It used to unpack the file if the file is packed for better behavior and function
BINTEXT Tool
· Tool used to analyze the Strings
· Libraries and Functions
· URL, IP address and File path
· Display message, Reg path
PE STUDIO Tool
· It is used to analyze the PE
Header
· It is a portable and free program
which is able to examine the executable file in depth
· Number of Indicators, Sections,
Libraries, Resources, and Functions
· Dos- header
BASIC DYNAMIC MALWARE ANALYSIS
Dynamic malware analysis involves a thorough analysis using the behavior and actions of the
malware sample while in execution to have a better understanding of the sample.
TOOLS
REG SHOT Tool
· It is used to check the behavior of
a system before running the malware in the first shot and after running the
malware in the second shot.
· Keys and values modified can see after comparing the first and second shots.
AUTORUN TOOL
· Mainly understand for persistence
mechanism.
· Autorun is used to check whether the malware is
trying to start any new process after the execution is done.
·
It is
process monitor tool
·
Mainly
used for file modifications
ü
Modify
file
ü Read file
FAKENET TOOL
· Fakenet is used to get to know
what server or traffic is going to contact.

Setting up the Analysis Environment
· Install VM
· Install Windows 10
· Download and Install FlareVM
(Platform designed for reverse engineers, malware analysts, incident
responders, fornicators, and penetration testers)
· Disable Firewall and Antivirus
Beginning Dynamic Analysis with AUTORUN
· Run AUTORUN as administrator and
leave for a couple of seconds so that all processes will execute.
· Save non-infected image
· Run test Malware
· Compare with a known good baseline
(saved non-infected image)
· You will find
the difference, Forex- An additional process is showing (on screenshot)
· As you see, it
is showing the complete path of the file and indicating ‘Task Scheduler’
· Now will go to
‘Task Scheduler’ to check
· Locate ‘Service
Update’ which was showing on the above screenshot
· Investing
schedule Task – By double click on task ‘Service Update’
· Check all the
options, like - General, triggers,
actions …. You will find a variety of details.
· Below
Screenshot for your references.
Then execute
‘Process Monitor’ to check changes in Processes.
· Filter only
that particular file ‘Usjdltufs.exe’
· Disable all the
processes, except Network process
· Compare
parallelly Network Traffic on Wireshark and Procmon
· Investigate
deep on Wireshark and compare the process from Procmon to Wireshark
filtered by time.
· Like in above
screenshot – you can find standard query on ‘api.ipify.org’ from our machine
(10.0.2.15) to google DNS server (8.8.8.8)
· Then in below screenshot,
you can find (highlighted in red)-
Connection/call out from local machine to remote machine
(54.243.136.64) over TCP on port 80
· You can find 2-way connection b/w our machine
and remote server and proper handshake with acknowledgment and finishing (ACK,
FIN)
· This remote IP
could be attacker IP and ‘api.ipify.org’ could be malware.
· You need to
take knowledge for Flags (Syn, Ack, Win …)
· Let’s figure
out where this TCP connection is going to so that we can block them on
firewall
· Right-click on
packet > Follow > TCP Stream (Below screenshot)
· You can see “Keep
Alive” connection. (Keep-Alive connection means a standard request to a webpage and
requests an IP address back )
· Only ‘keep-alive’ connection because this is
only a training malware. If not, it could be anything. Like root access, remote
access
Files and folder created
·
Let’s check modification in malware location on a local machine
·
As you can see, there are 3 more folders with .exe file
(malware file)
Module – To download malicious content where the connection is made
Client ID – (Below screenshot)
Group Tag- (Below screenshot)
CONCLUSION
• Install Anti-Virus/Malware Software. ...
• Keep Your Anti-Virus Software Up to Date.
...
• Run Regularly Scheduled Scans with Your
Anti-Virus Software. ...
• Keep Your Operating System Current. ...
• Secure Your Network. ...
• Think Before You Click
Keep Learning :D Subscribe to blackhatsec-mrfu3k



























Comments
Post a Comment