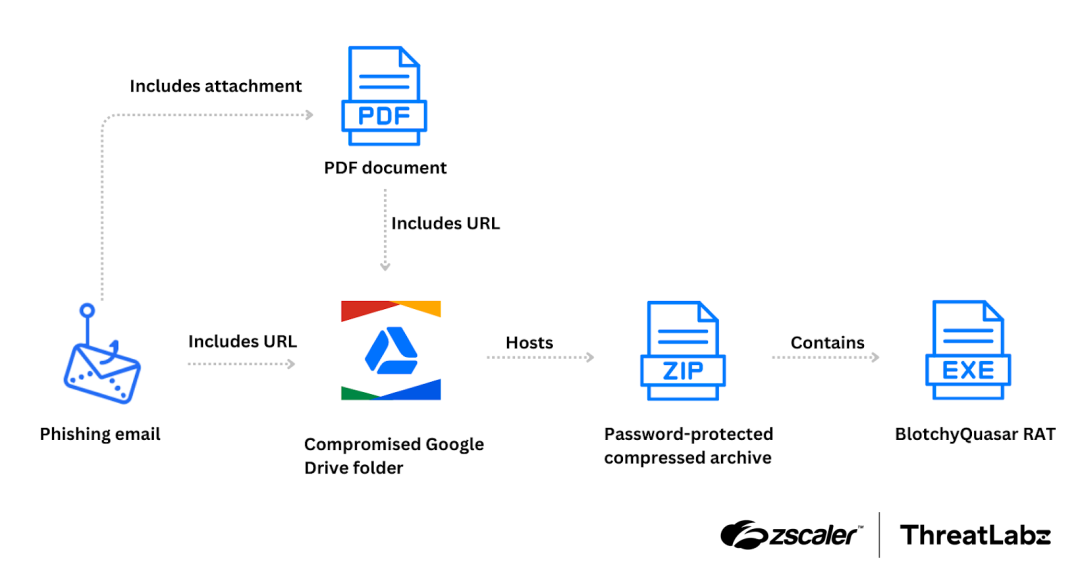
A BlindEagle attack chain typically originates with a phishing email that contains a PDF attachment and a URL that points to a ZIP archive file. The PDF attachment contains the same URL as the one provided in the email body. In other words, the ZIP file can be either downloaded from the PDF or directly from the email.
Upon clicking the URL (in either the email body or PDF), the victim downloads a ZIP archive from a Google Drive folder. This specific folder is under the ownership of a compromised account belonging to a regional government organization in Colombia. The ZIP archive contains a .NET BlotchyQuasar executable.
The figure below provides for a high-level overview of the attack chain.
The Colombian insurance sector is the target of a threat actor tracked as Blind Eagle with the end goal of delivering a customized version of a known commodity remote access trojan (RAT) known as Quasar RAT since June 2024.
"Attacks have originated with phishing emails impersonating the Colombian tax authority," Zscaler ThreatLabz researcher Gaetano Pellegrino said in a new analysis published last week.
The advanced persistent threat (APT), also known as AguilaCiega, APT-C-36, and APT-Q-98, has a track record of focusing on organizations and individuals in South America, particularly related to the government and finance sectors in Colombia and Ecuador.
The attack chains, as recently documented by Kaspersky, originate with phishing emails that entice recipients into clicking on malicious links that serve as the launchpad for the infection process.
The links, either embedded within a PDF attachment or directly in the email body, point to ZIP archives hosted on a Google Drive folder associated with a compromised account that belongs to a regional government organization in Colombia.
"The lure used by Blind Eagle involved sending a notification to the victim, claiming to be a seizure order due to outstanding tax payments," Pellegrino noted. "This is intended to create a sense of urgency and pressure the victim into taking immediate action."
The archive contains within it a Quasar RAT variant dubbed BlotchyQuasar, which packs in additional layers of obfuscation using tools like DeepSea or ConfuserEx to hinder analysis and reverse engineering efforts. It was previously detailed by IBM X-Force in July 2023.
The malware includes capabilities to log keystrokes, execute shell commands, steal data from web browsers and FTP clients, and monitor a victim's interactions with specific banking and payment services located in Colombia and Ecuador.
It also leverages Pastebin as a dead-drop resolver to fetch the command-and-control (C2) domain, with the threat actor leveraging Dynamic DNS (DDNS) services to host the C2 domain.
"Blind Eagle typically shields its infrastructure behind a combination of VPN nodes and compromised routers, primarily located in Colombia," Pellegrino said. "This attack demonstrates the continued use of this strategy."



Comments
Post a Comment